SQL injection is a code injection technique, used to attack data driven applications like stSoftware.
stSoftware systems support a number of web accessible protocols including:-
- ReST
- SOAP
- Web Forms
- GWT RPC
All protocols access the underlying data through the DAL ( data access layer). There is NO direct access to the underlying data store no matter which protocol is used. Each protocol accepts the request to read or write data and then perform the protocols validations and then passes the request on to the DAL to execute the request which in turn validates the request, checks the user's access and perform any validations before returning the result.
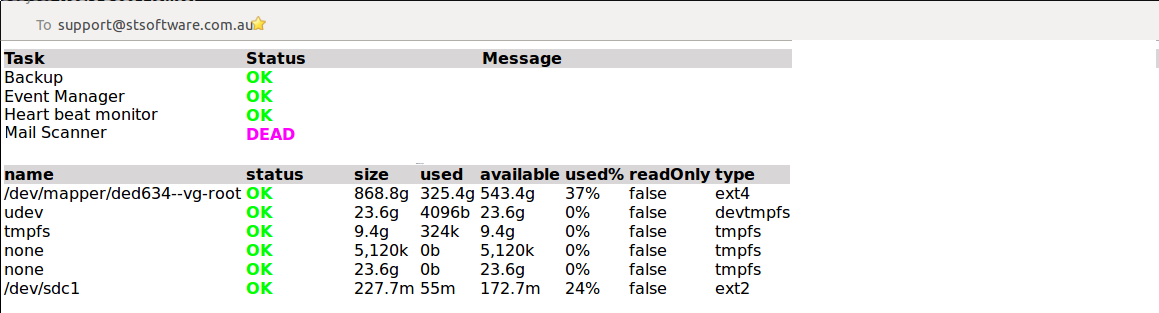
SQL & XSS attacks are automatically tested for each of the supported protocols. Listed below are the standard SQL injection strings attempted.
| SQL Injection String |
| "&%00<!--\'';你好 |
| \'; DROP |
- 14 Mar 2014
Overview
Single sign using Microsoft LAN Manager (NTLM) allows users within a intranet enviroment to use the system without the need to re-enter their password once they have logged into the Windows network.
Note the NTLM protocol can only be used within a internet environment.
- 2 Mar 2014
Overview
All Linux servers are locked down to the highest security standards possible. All services are off by default and all ports shut. Only the required services started.
To lock down a server:-
-
- Install and run only the services you require.
- Block all ports by default and open only those that are required
- Run servers as low permission user
- Disable direct login to ROOT completely.
- Block SSH login attempts from unknown locations and machines.
- Set up tripwire to detect intrusions
- Increase file handles
- 26 Jan 2014
After you have registered a new domain name with a domain name (DNS) provider such goDaddy, or you have an exisiting domain name, you need to change the associated IP address so that your domain name points to stSoftware's servers.
Or contact us to add "Assigning your domain name" service to your website or websystem package and we'll manage it for you.
Assign your domain (host) name to the IP addresses of our servers
Have your DNS pointed to either of the two groupings of IP addresses below;
101
- 1 Jan 2014
Server Cluster
A cluster of servers (two or more ) can be setup and the DNS entry for your site can be defined with the IP addresses for each of the servers, this is known as Round-robin DNS
- 18 Dec 2013
When articles are published the built in social integration automatically posts the article to the requested social sites.
When posting to twitter the title and subtitle are automatically shorten to within the 140 character limit.
All published articles are automatically published via the RSS feed.
The CMS automatically generates an XML Sitemap which can be submitted to search engines for faster indexing of new content.
- 14 Dec 2013
There are many built in reports created in the screen painter.
Jasper Reports can be designed and uploaded for more complex reports
External tools such as Open Office or Excel can be used to generate reports via JDBC or ReST web services.
- 13 Dec 2013
Supported desktop browsers
Supported tablets
- iPad 2+ with iOS7+
- Android tables 4.3+
- 13 Dec 2013
Overview
stSoftware designs systems to meet or exceed all aspects of the Australian Government Protective Security Policy Framework PSPF. At stSoftware, we take security very seriously. Our ephemeral workload servers are locked down to be accessed only via bastion hosts; the support team can only access the bastion hosts themselves via secure shell from specific IP addresses.
stSoftware follows Infrastructure as Code principles for all AWS services.
- 13 Dec 2013
yes, the site owner can/should be able to change anything.
And technically they can as it's all just JavaScript/HTML/CSS.
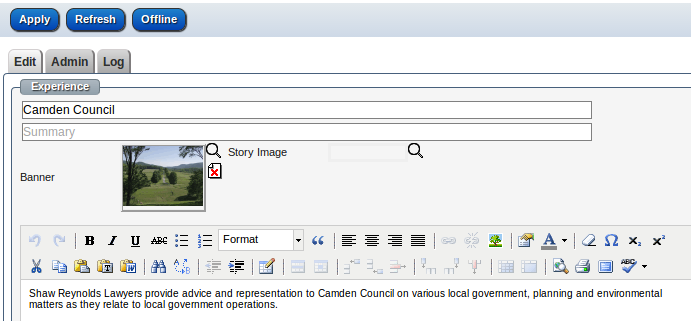
An example is SRL when they publish an article the banner image is placed on the carousel and linked to the article. The page reads this information from the RSS feed.
- 27 Nov 2013